Internal audit report outlining results of the assessment of the IT Security Review at Transport Canada as well as management's action plan in response to recommendations identified in the audit.
On this page
- Executive summary
- Statement of conformance
- 1. Introduction
- 2. Observations
- 3. Summary of recommendations and management action plan
Executive summary
The purpose of our examination was to determine if TC security related governance and management processes effectively address cyber security events.
We focused on the Detection and Assessment Phases of the Cyber Security Event Management Plan. This includes reviewing the monitoring of information sources, the detection and recognition of cyber security events and the triage and prioritization processes that follow.
Overall TC is aligning itself in accordance with the Treasury Board Secretariat (TBS) policies and directives related to IT Security. Senior management has been proactive in engaging GartnerFootnote 1, for example, to review the existing IT Security environment at TC. We also found a high level of engagement and commitment of IT Security resources with respect to managing and fulfilling their IT Security and incident management roles.
Gartner IT security review
Following Gartner's Security Management Maturity Benchmark Assessment Report, TC's Cybersecurity Manager was assigned the task of managing the process of coordinating the development of an action plan to address the recommendations. To date, only a few management action plans to address the Gartner report recommendations have been developed. Therefore we recommend that the department develop action plans to address the cyber security gaps identified by Gartner that represent potential threats to TC's ability to deliver its programs and services. The progress implementing these action plans should be regularly communicated to senior management. Overall Gartner found that TC's security posture was defined and on par with other Government departments.
Transport Canada Incident Response Procedures
A well-defined response plan allows organizations to effectively respond to potential incidents in order to minimize their impact and cost while finding and fixing the cause to prevent future attacks. We expected that incident response procedures be streamlined and kept current and updated based on lessons learned from incidents, to help ensure incidents are handled in a timely and efficient way.
The existing Incident Response Procedures document is more of a roles and responsibilities document than an actual procedures guide. It provides a lot of details describing the various internal and external partners to the Government of Canada but does not clearly and simply describe the steps to be taken in the event of a cyber security incident.
We recommend a simple and clear procedures document to help TC respond efficiently and effectively to a cyber security event. The procedures will guide teams on how to react to computer security incidents, determine their scope and risk, respond appropriately to the incident, and how to communicate the results and risk to stakeholders.
Service Level Agreements between Transport Canada and partners
TC's cyber security incidents are managed in conjunction with its government partners who include the Canadian Center for Cyber Security (CCCS) and Shared Services Canada (SSC). There needs to be coordinated efforts from all teams to resolve cyber security incidents in an effective manner. The ability for TC's Security team to manage the IT environment is largely dependent on the response time of TC's external partners. At present, there are no Service Level Agreements (SLAs) in place between TC and their partners.
We found that TC IT Security employees do not have timely access to information required to evaluate cyber security incidents and/or do not have delegated access to information/systems to support timely detection and effective response to cyber security events.
We recommend two SLAs be developed. One between TC and CCCS and another between TC and SSC as they both provide source information required by TC to review potential incidents and make informed decisions.
Reporting of incidents to senior management
Senior management and especially the Deputy Minister (DM) needs to be made aware of critical incidents which may impact TC's IT operating environment. To help ensure timely communication we expect there are clear criteria for determining which TC organization should be communicating incidents to the DM, and that there is a streamlined process to debrief the DM in the event of critical incidents.
Currently, there are three organizations within TC that can report security incidents to the Deputy Minister: the Chief Digital Officer (CDO), Chief Security Officer and the DG Emergency Preparedness. Despite the existing process, due to the nature of these incidents, it is not always clear who/what and when the details should be communicated to the DM since there are three separate functions reporting security incidents to the DM. We recommend a standard process be defined for briefing incidents to the DM and ensuring appropriate communication with all key stakeholders.
Cybersecurity metrics
There are many reasons why cyber security metrics are produced to support a robust cyber security program. Gathering security metrics would allow TC to help senior management in their decision making. We expected relevant and useful cyber security metrics would be reported on a regular basis to senior management to support their decision making. Although, cyber security metrics are reported in quarterly reports provided to the CDO the relevance and usefulness of the indicators needs to be improved. The CDO with input from senior management should develop relevant and useful indicators including the processes for collecting and analyzing the data to better support cyber security related decision making.
Statement of conformance
This Audit conforms to the Internal Auditing Standards for the Government of Canada, as supported by the results of an external assessment of Internal Audit's Quality Assurance and Improvement Program.
Dave Leach
(CIA, MPA) Director, Audit and Advisory Services
Martin Rubenstein
(CPA, CIA, CFE) Chief Audit and Evaluation Executive
1. Introduction
1.1 Purpose
The 2019-2020 Risk Based Audit Plan includes an examination of IT Security management of cyber security incidents) which is intended to coincide with the Office of the Comptroller General's (OCG) IT Security Review Phase 2: Cybersecurity Detection and Assessment of the GoC Cybersecurity Event Management Plan (GC CSEMP).
Background
The Treasury Board of Canada defines cyber security as the body of technologies, processes, and practices designed to protect electronic information and information infrastructure from mischief, unauthorized use, or disruption; a subset of the processes and practices of IT security, which includes the broader application of policies and people-focused security management techniques.
Cyber security
"Cyber security events related to Government of Canada (GC) information systems can have a significant impact on the delivery of government programs and services to Canadians and, consequently, confidence in government. The ability to respond to cyber security events in a consistent, coordinated and timely manner across the GC is essential to ensure the security and resilience of GC program and service delivery."
Government of Canada Cyber Security Event Management Plan (GC CSEMP) 2018 (PDF, 1.3 MB)
According to Verizon's Data Breach Investigations Report 2018, 74 percent of cyber security breaches in the public sector are initiated by phishing emails. Sixty-eight percent (68%) of breaches took months or longer to be discovered, in many cases by a third party such as a partner/service provider instead of the organization itself. One of the main recommendations of the report is to make an organization's employees the first line of defense.
The Standing Senate Committee on Banking, Trade and Commerce published a report "Cyber Assault: It should keep you up at night" in October 2018. Whilst the committee acknowledged some progress had been made federally, the report makes clear that more cyber security education is needed in Canada. "Cyber resilience" refers to an institution's ability to anticipate, withstand, contain and rapidly recover from a cyber-attack before it compromises operations or harms its customers. Becoming more cyber resilient is the joint responsibility for governments, the private sector and consumers as they each play a role in protecting key networks from cyber threats. One of the report's recommendations states that all levels of government must prioritize cyber security education as part of the National Cyber Security strategy (PDF, 566 KB).
A security breach is any incident that results in unauthorized access of data, applications, services, networks and/or devices through bypassing their underlying security mechanisms. Cybersecurity breaches are rising in organizations of all sizes around the globe resulting in both financial and reputational losses.
Government of Canada Cyber Security Event Management Plan (GC CSEMP) 2018
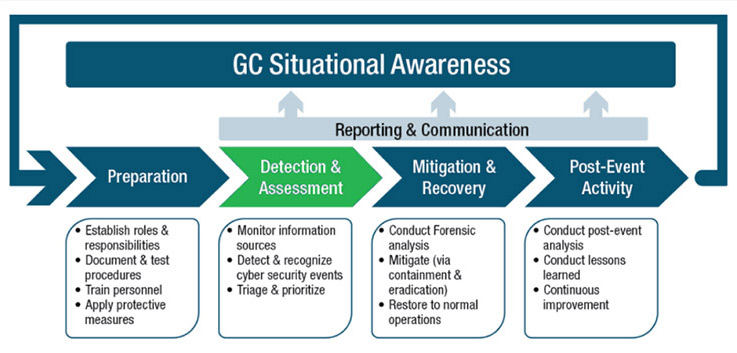
Federal departments follow the GoC operational framework for the management of cyber security events. The following figure illustrates the Government of Canada Cyber Security Event Management Plan (GC CSEMP) 2018. The green highlighted chevron is the Detection and Assessment phase.
Long description
This graphic illustrates the overall cyber security event management process defined in this document has several phases. The initial phase, preparation, involves general readiness activities to ensure that the GC is ready to respond to the broad range of cyber security events. In this phase, event-related roles and responsibilities are established, plans and procedures are documented and exercised, personnel are trained and protective measures are applied. The second phase highlighted and the focus of our review is detection andamp; assessment, involves the discovery of potential cyber security events, initial assessment and triage of incidents and confirmation of cyber security incidents, through the monitoring of various sources (including departmental and GC wide solutions) The third phase, mitigation & recovery, consists of all response actions required to minimize impacts to confidentiality, availability and integrity, and lead to restoration of normal operations. Containment and eradication are key components. Recovery actions include measures that will allow for a return to normal operations. This phase also includes root cause analysis and investigation, which consist of activities such as forensic analysis. The final phase, post-event activity, is vital for continuous improvement of the overall cyber security event management process and feeds back into the preparation phase to complete the event management life cycle. This phase consists of post-event analysis, conducting lessons learned and recommending changes to processes or procedures in order to improve the GC's cyber security event management process.
GoC digital operations
A new Government of Canada Digital Policy is being developed and is to be launched April 1st 2020. Its aim is to further integrate technology and data in all stages of the processes for policy, program and service delivery. This will be achieved through a single set of rules and guidelines for government departments and agencies that will set out how the Government of Canada manages service delivery, information and data, technology and cyber security. This will re-position cyber security to the forefront and hopefully provide more direction on roles and responsibilities of government departments over the governance and management of cyber security.
Similarly the refresh of the Policy on Government Security was released on July 1, 2019. It outlines the roles and responsibilities of Deputy Heads, lead security agencies and internal enterprise service organizations in managing government security controls in support of the delivery of services and programs in protecting information, individuals and assets. This includes the provision for managing cybersecurity.
In March 2018 TC's CIO, requested a detailed security review of IT within the department. GartnerFootnote 2 was engaged to review TC's IT security environment which included identifying and evaluating security risks and mitigation capabilities using criteria based on industry leading practices. Gartner delivered their report, "Security Management Maturity Benchmark Assessment" in June 2018"Footnote 3.
Canadian Center for Cyber Security (CCCS)
A new National Cyber Security Strategy (PDF, 566 KB) was introduced by the federal government in 2018 as well as a new Canadian Centre for Cyber Security. The Cyber Centre is part of the Communications Securities Establishment (CSE) and is positioned as the single unified source of expert advice, guidance, services and support on cyber security for government, critical infrastructure owners and operations, the private sector and the Canadian public. The CCCS has initiated a new framework for managing cyber security which all federal departments follow. In addition, interactions with SSC are now coordinated via the CCCS.
At Transport Canada
With the establishment of the new Canadian Centre for Cyber Security and the nature of the elevated need for robust cyber security, Transport Canada has had to adapt and clarify its IT security roles and responsibilities. With this new cyber environment a need for additional resources was identified to help fulfill the new roles/responsibilities associated with cyber security. Subject to funding availability, TC's Digital Services Directorate (DSD) is proposing to hire two new employees to meet the demands of managing cyber security.
The Office of the Comptroller General's IT Security Audit
Phase 1 "Horizontal Internal Audit of Information Technology Security in Large and Small Departments" was published in February 2016. It focused on the Preparation Phase for Cyber Security. The audit noted a need for improvements to both governance frameworks and controls over IT security within departments, as well as across government, to mitigate IT security risks and properly safeguard government systems against rapidly evolving threats
Although Transport Canada was not included in Phase 1, TC is included in the second part of the OCG horizontal audit, "Blended Horizontal Engagement of Information Technology (IT) Security Phase II" Footnote 4 which is focusing on the Detection and Assessment phase of the GoC Cybersecurity Event Management Plan (GC CSEMP) (see Figure 1: GC CSEMP above). This Phase is anticipated to be completed by the end of the fiscal year 2019/2020.
Specifically this part of the OCG audit, aimed at large departments, is trying to determine if IT security awareness and training as well as technical controls effectively support incident detection of social engineering, endpoint attacks, and cloud data breaches.
1.2 Audit objective, scope, approach, and criteria
1.2.1 Audit objective
To determine if TC security related governance and management processes effectively address cyber security events.
1.2.2 Audit scope
We focused on the Detection and Assessment Phases of the Cyber Security Event Management Plan (see above Figure 1: GC Cyber Security Event Management Plan). This includes reviewing the monitoring of information sources, the detection and recognition of cyber security events and the triage and prioritization processes. Specifically, we examined:
- the adequacy of TC cyber security standards and procedures and their operating effectiveness
- the effectiveness of the response and recovery programs (whether incidents / breaches are identified in a timely and appropriate manner)
It is important to note that the effectiveness of the security awareness program is also being assessed through the OCG led Spear Phishing simulation, the EndPoint simulation and Cloud simulation testing. The results of this testing will be reported separately from this report once the OCG led exercise is completed, which is anticipated for late winter fiscal year 2019/2020.
1.2.3 Audit approach
As Gartner's review comprised a full end to end security assessment of governance and management over security, operations, and technical controls, our assessment has leveraged this work as much as possible to avoid duplication.
To determine whether the Gartner Security Management Maturity Benchmark Assessment Report adequately covered the detection/assessment phases of the cyber security event management process (see Figure 1: GC Cyber Security Event Management Plan), we compared Gartner's coverage against an audit program from the United States National Institute of Standards and Technology (NIST) Cybersecurity FrameworkFootnote 5 which outlines expected controls related to detection and assessment for a typical cyber security review. Based on our crosswalk, Gartner's assessment covered all the functional areas contained within the ISACA/NIST Audit Program except the following (related to Incident reports):
- review of incidents and associated incident reports
- whether incident response testing is performed
In addition to ensuring our work covered the two areas not examined by Gartner, we also worked with TC's IT Security Team to help improve the department's cyber security posture by flow charting and documenting cyber security processes.
1.2.4 Audit criteria
- management action plans have been developed to address the findings of the Gartner IT Security Review
- roles and responsibilities related to cyber security between TC and the External Partners are clearly defined and communicated
- there is an effective process in place to support detection and assessment of incidents in a timely manner
- cyber security risks and incidents are effectively communicated to senior management in a timely manner
1.3 Report structure
For ach observation we have included contextual information, a summary of what we expected, what we found, and where appropriate, recommendations. The last section of the report summarizes the recommendations and includes management's action plan.
2. Observations
Overall conclusions
Overall TC is aligning itself in accordance with the TBS policies and directives related to IT Security. Senior management has been proactive in engaging Gartner, for example, to review TC's existing IT Security environment. And the department has a small, skilled and engaged IT Security team who oversee Cyber Security and the incident management process.
Engaging Gartner to identify IT security gaps and areas of improvement was an important exercise but it has been taking too long to address the findings. As well, although there are incident response procedures the current guidance does not provide simple step by step guidance that can easily be followed when incidents occur.
TC (DSD-IT Security) has highlighted some teething pains under the new CCCS organization framework for cyber security management. Most notably the lack of Service Level Agreements (SLA)/MOU. A SLA/MOU is necessary between TC and CCCS to help ensure that internal requests made by TC IT Security to CCCS are being responded to within agreed upon timeframes. Currently as TC IT Security engage with CCCS regarding potential incidents there is inconsistency in the timeliness of responses. In addition, a SLA between TC and SSC is important for internal requests made by TC related to network, email, firewall and telecoms which could experience potential cyber incidents.
The reporting of cyber related incidents within TC are not reported up to the DM in a standard fashion. There is currently no repeatable process to inform the DM of cyber related incidents. This leads to confusion at the senior management level as it is entirely dependent on the accurate determination of the type of incident reported and its ownership.
Given the increasing importance of effective cyber security management, senior management needs relevant and useful performance indicators (cyber security metrics) to better support decision making:
- at the operational and strategic levels of the organization
- to help further develop its cyber security program
- to continuously improve performance of the teams responding to cyber security events
Better cyber security metrics will help TC to continuously improve its capability to respond to cyber security events and strengthen its cybersecurity posture.
2.1 Lack of management action plans (Re: Gartner Security Management Maturity Benchmark Assessment Report – GSMMBAR)
Context
Following Gartner's Security Management Maturity Benchmark Assessment Report, TC's Cybersecurity Manager was assigned the task of managing the process of coordinating the development of an action plan to address the twenty-five recommendations.
The recommendations were based on end to end assessments of the TC information technology infrastructure and security architecture, security governance, compliance and risk management, security operations, access control, end user access methods, data protection, physical security of IT assets, availability, IT asset management and management of technical vulnerabilities.
The report found there was a need to review the security resource requirements in order to address the significant security gaps identified. These included a lack of a comprehensive cyber security risk management program in alignment with CSE guidelines, undefined responsibilities for security governance, a lack of data and information classification and protection, gaps in business system resilience, undefined department strategy for security, monitoring alerting and response, and, a need for end to end application security including code security reviews and automated security testing.
Expectations
We expected that the Gartner results would have been communicated to stakeholders and an overall Management Action Plan would have been developed to address the gaps identified in the report.
What we found
As at the time of our examination, only a few management action plans to address the Gartner report recommendations had been developed. Despite attempts by the Cybersecurity Manager to obtain management action plans from the various OPIs across DSD, as of June 2019, eight percent (8% or 2 out of 25) of management action plans had been received.
The majority of the DSD stakeholders responsible for contributing to developing management action plans understand their importance. However they consistently cite too many competing priorities have taken precedence. In addition, the gaps identified had not been communicated to all senior management via either TMX or other senior level committees.
Why it is important
It is important to develop and implement management action plans to address the identified cyber security gaps that represent potential risks to TC's ability to deliver programs and services to Canadians.
Recommendation
Develop management action plans to address the gaps identified in the Gartner Security Management Maturity Benchmark Assessment Report and regularly communicate implementation progress to senior management (for example, TMX).
2.2 Update required to incident response procedures/documentation
Context
There is a TC Cybersecurity Incident Response Procedures document which was originally created in 2010 and more recently amended, first in 2018 and most recently in April 2019 to reflect the roles and responsibilities of the CCCS. The last two significant Cybersecurity incidents occurred in February and March 2019 before the Incident Response Procedures document was last amended.
The GoC Cyber Security Event Management Plan (GC CSEMP) outlines the need for "developing, maintaining and testing departmental cyber security event management plans and processes", and to test, at a minimum annually, their Incident Response procedures to ensure that they are effective in the event of a cyber security incident.
Expectations
We expected streamlined incident response procedures that are kept current and updated based on lessons learned from incidents, to help ensure incidents are handled in a timely and efficient way.
What we found
The Incident Response Procedures document is more of a roles and responsibilities document than an actual procedures guide. It provides a lot of details describing the various internal and external partners to the Government of Canada but does not clearly and simply describe the steps to be taken in the event of a cyber security incident. The roles and responsibilities at the various stages of the incident event management lifecycle would prove difficult to follow in the event of an actual incident. For example, the procedures should describe the interaction between TC and the CCCS and the specific steps each should take when an incident occurs. Instead, the TC IT security team relies solely on their knowledge, skills and experience in responding to incidents.
Following the Corporate Online Payment System incident (February 2019), two procedural "lessons learned" recommendations were issued: one related to handling the priority of tickets in the event of cyber incidents, and the other making sure that changes to the configuration of systems is captured and readily available. Both of these recommendations are important and warrant inclusion in the Incident Procedures. However at the time of our examination they had not been reflected in the TC Incident Procedures document.
Why it's important
A simple and clear procedures document will help TC respond efficiently and effectively to a cyber security event. The procedures will guide teams on how to react to computer security incidents, determine their scope and risk, respond appropriately to the incident, including how to communicate the results and risk to all stakeholders.
Recommendation
To improve the guidance available to effectively manage cyber security incidents, adding the following elements to Incident Response Procedures should be considered:
- define criteria and procedures to triage incidents
- create a short consistent list of response steps for each major incident type
- define what constitutes a "significant" or "severe" security incident to ensure escalation to the appropriate level of TC senior management and update the Cybersecurity Escalation table contact list to reflect this
- establish a regular testing protocol to ensure readiness and ability to respond effectively
- require lessons learned exercises after tests and/or incidents and incorporate the resultant recommendations into the Incident Procedures document to enable continuous improvement
- review and update annually, or upon change of operating environment (cloud adoption for example) or following an incident
2.3 Formalize Service Level Agreements between TC and external partners supporting cyber security
Context
The ability for TC Security teams to manage the IT environment of TC users is dependent on the response time of TC's external partners. The current IT operating model between TC and SSC and TC and the CCCS creates a gap in the level of service required to effectively respond to a cyber security incident. {ATIP Removed}
Expectations
We expect Transport Canada's service requirements be defined and documented in Service Level Agreements (SLAs) between TC and its partners (CCCS/SSC) with definitions of triggers and thresholds, for the various services.
What we found
We found that TC IT Security employees do not have timely access to information required to evaluate cyber security incidents and/or do not have delegated access to information/systems to support timely detection and effective response to cyber security events. There needs to be better coordinated efforts from all teams to resolve cyber security incidents in an effective manner.
The following ‘email account' example illustrates the need for Service Level Agreements for a variety of services. The email exchange gateway is managed by SSC. Review of email logs is mainly a manual subjective process. The SSC analyst is expected to notice anomalies such as large increases of emails being sent by TC and/or large increases of emails being received by TC from specific domains.
For example, if a TC account is seen sending a relatively large number of emails within a small time period, SSC may suspend the TC email account to prevent more emails from being sent, then create a ticket of the actions taken and notify TC. This externally managed process is prone to error and there are no established thresholds for suspending an email account.
Why it's important
Agreements defining the roles, responsibilities and expectations between an external service partner (CCCS and SSC) and TC are important to ensure accountability. The objective of a SLA is to present a clear, concise and measurable description of what the service provider does for the customerFootnote 6. The current lack of ready access to information/tools hampers TC's ability to respond to potential incidents and provide efficient IT security to its internal clients. TC needs more visibility into their networks and better service delivery from SSC to effectively monitor and oversee their environment.
In addition, there is a new requirement outlined within the Policy on Government Security (section 4.1.7) which requires a Deputy Head to "establish a written agreement when the department relies on or supports another department or organization to achieve government security objectives".
Recommendation
We recommend two SLAs be developed between TC and CCCS and TC and SSC as they both provide source information required by TC to review potential incidents and make informed decisions. The SLAs should outline agreed to service terms such as:
- standard response times for various TC requests and indicators to ensure they are meeting targets
- service levels for routine tasks that SSC performs for TC
- visibility/transparency of the environment
2.4 Reporting to Senior Management (Roles and Responsibilities, Cyber Security Metrics)
Context
According to the ISACA Research Report: Better Tech Governance Is Better For Business cyber security is the number one corporate governance technology challenge, yet only 21% of organizational leaders are briefed on risk topics at every senior management meeting. In general up to 50% of an organization's systems are not critical from a cyber perspective therefore an organization needs to prioritize and focus valuable cyber security resources. Overall 87% of board level directors and C-level executives say they lack confidence in their organization's level of cyber security.
2.4.1 Roles and Responsibilities Cyber Security Management
Context
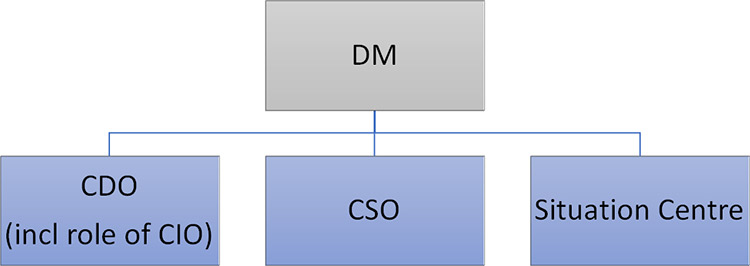
There are a number of types of internal security related incidents which the department deals with on a regular basis. For the purpose of our work, we specifically reviewed cyber security incidents that effect the department. There are three organizations within TC that can report security incidents to the Deputy Minister:
- Chief Digital Officer (Digital SD, CIO)
- Chief Security Officer (CSO)
- Situation Centre (DG, ISSEP and Executive Director, Emergency Preparedness)
The CDO is accountable for the CIO, DSD and cyber security. The Chief Security Officer and TC's Situation Center, in the event of a significant incident, have responsibilities as well to brief the DM.
Expectations
To help ensure timely communication we expect there are clear criteria for determining responsibility and a streamlined process to debrief the DM in the event of critical cyber security incidents. Determining the ownership of cyber security versus other security incidents is critical to sorting out reporting roles and responsibilities.
What we found
All security incidents deemed "severe" or "significant" are communicated to the Chief Security Officer (CSO). However, what constitutes a severe or significant incident has not been defined either within the internal TC documentation or within the GC Policy Suite. Cyber security incidents are initially recorded within the Incident Problem Management System once they become known to TC. DSD operates the system and once the incident is recorded a process is followed, where a triage is performed and the incident details are routed. All teams within DSD are to follow the incident management process implemented within DSD.
Despite the existing process, due to the nature of these incidents, it is not always clear who/what and when the details should be communicated to the DM. An example of this was the recent "robocall" incident. During the reporting process to the DM, there was uncertainty of which group should brief the DM. There were differing opinions and, as a result, the incident was not communicated in a timely manner.
The assessment and assignment of ownership of security events is not well understood within TC due to a lack of clarity over which incidents are cyber related or not. With three separate functions that can report security incidents it is unclear what kind of incidents should be reported up to the DM and by whom. This lack of a pre-defined communication process hampers senior management's ability to make decisions and provide direction.
Why it's important
Senior management and especially the DM needs to be made aware of critical incidents which may impact TC's IT operating environment.
Recommendation
A standard process should be defined for briefing cyber security incidents to the DM while ensuring appropriate communication with all key stakeholders.
The exercise to define a standard process should include defining what constitutes a "severe/significant" cyber security incident to help guide the type and level of communications needed for implicated stakeholders.
The Chief Security Officer role, as outlined within the refreshed Policy on Government Security (PGS) has already been assigned within TC. Specifically the Chief Security Officer is to be "responsible to the deputy head or to the departmental executive committee to provide leadership, coordination and oversight for departmental security management activities". There is an opportunity for this role to be further clarified as it relates to cyber incidents.
2.4.2 Reporting cyber security metrics
Context
Cyber security metrics support a robust cyber security program by gathering security metrics that allow organizations to:
- communicate cyber security related performance
- measure the effectiveness of IT controls and help drive performance improvementFootnote 7
Expectations
We expected relevant and useful cyber security metrics would be reported on a regular basis to senior management to support their decision making.
What we found
Cyber security metrics are reported in quarterly reports provided to the Chief Digital Officer. These metrics are primarily based on available data received from the third-party providers (McAfee, SSC, CCCS) and records from the Incident Problem Management System. All types of incidents, such as malware, compromised computers, lost/stolen devices etc., are reported regardless of their severity. The relevance and usefulness of these cyber security metrics is unclear. Senior management has not been engaged to help define key performance indicators (KPIs) that would best support their decision making related to cyber security.
Why it's important
Regular reporting of relevant and useful KPIs will support senior management to make informed decisions related to safeguarding TC's data assets.
Recommendations
The Chief Digital Officer with input from senior management should develop relevant and useful performance indicators including the processes to collect, analyze and report the results to better support cyber security related decision making. Examples of potential indicators could include the number of:
- significant IT-related incidents that were not identified in a risk assessment
- confidentiality incidents with the potential to cause financial loss, business disruption or public embarrassment
- customer service or business process interruptions causing significant incidents Business cost of incidentsFootnote 8
3. Summary of recommendations and management action plan
The following summarizes the audit recommendations and management's plan to address them.
| # | Recommendation | Management action plan | Date (for each action) |
Office of Primary Interest (OPI) |
|---|---|---|---|---|
| 1. | Develop management action plans to address the gaps identified in the Gartner Security Management Maturity Benchmark Assessment Report and regularly communicate implementation progress to senior management (for example, TMX). |
Digital Services will:
|
May 2020 | Digital Services |
| 2. |
To improve the guidance available to effectively manage cyber security incidents, adding the following elements to Incident Response Procedures should be considered:
|
Digital Services will:
|
May 2020 | Digital Services (Offices of Collateral Interest: CSO, Emergency Preparedness) |
| 3. |
We recommend two SLAs be developed between TC and CCCS and TC and SSC as they both provide source information required by TC to review potential incidents and make informed decisions. The SLAs should outline agreed to service terms such as:
|
Digital Services will:
|
May 2020 | Digital Services/CSE/SSC |
| 4. |
4.1 A standard process should be defined for briefing cyber security incidents to the DM while ensuring appropriate communication with all key stakeholders. 4.2 The Chief Digital Officer with input from senior management should develop relevant and useful indicators including the processes to collect, analyze and report the data to better support cyber security related decision making. Examples of potential indicators could include the number of:
|
4.1 Digital Services will work with Departmental Security to develop and implement a standard process for briefing significant cyber security incidents to the DM while ensuring appropriate communication with all key stakeholders. 4.2 Digital Services will:
|
4.1 - May 2020 4.2 - May 2020 |
Digital Services (Offices of Collateral Interest: CSO, Emergency Preparedness) |